New AI-Powered Android Malware Hijacks Millions of Devices for Invisible Ad Fraud
Zero-days, exploit breakdowns, IOCs, detection rules & mitigation playbooks.
INCIDENT ANALYSIS REPORT: OPERATION "GHOST FINGER"
Status: CRITICAL | Incident ID: 2026-ADV-04-GF | Date: January 22, 2026
Executive Summary
A new generation of Android malware, identified by researchers as "ClickWise AI" (or the Ghost Finger strain), has successfully compromised millions of devices globally. Unlike traditional ad-clickers that rely on static scripts, this threat utilizes a local TensorFlow.js machine learning model to conduct unauthenticated, human-mimicking ad fraud. By visual analysis of the UI, the malware identifies ad elements and performs "invisible" clicks in a hidden background layer, bypassing modern anti-fraud telemetry.
CyberDudeBivash’s Bottom Line: This is the first industrial-scale application of Agentic AI in mobile malware. It doesn't just "click links"; it observes and decides. Traditional bot-detection filters looking for repetitive patterns are essentially blind to this behavior.
Technical Vulnerability & Attack Surface
The malware primarily exploits the Android Accessibility Services and WebView components to gain administrative-level control over the device interface without user consent for specific actions.
Key Technical Mechanisms
TensorFlow.js Visual Analysis: The malware takes background screenshots of a "virtual screen." The AI model analyzes these images to locate "Close" buttons, "Install" prompts, and "Video Ad" play buttons.
Phantom Mode (Hidden WebView): It renders a hidden browser layer. To the user, the phone appears idle; in the background, a high-velocity ad-bidding war is being engaged by the malware.
Behavioral Masking: The AI adds "human jitter" (variable tap duration, non-linear scrolling, and hesitation delays) to every interaction, making the traffic appear as high-value human engagement to advertisers.
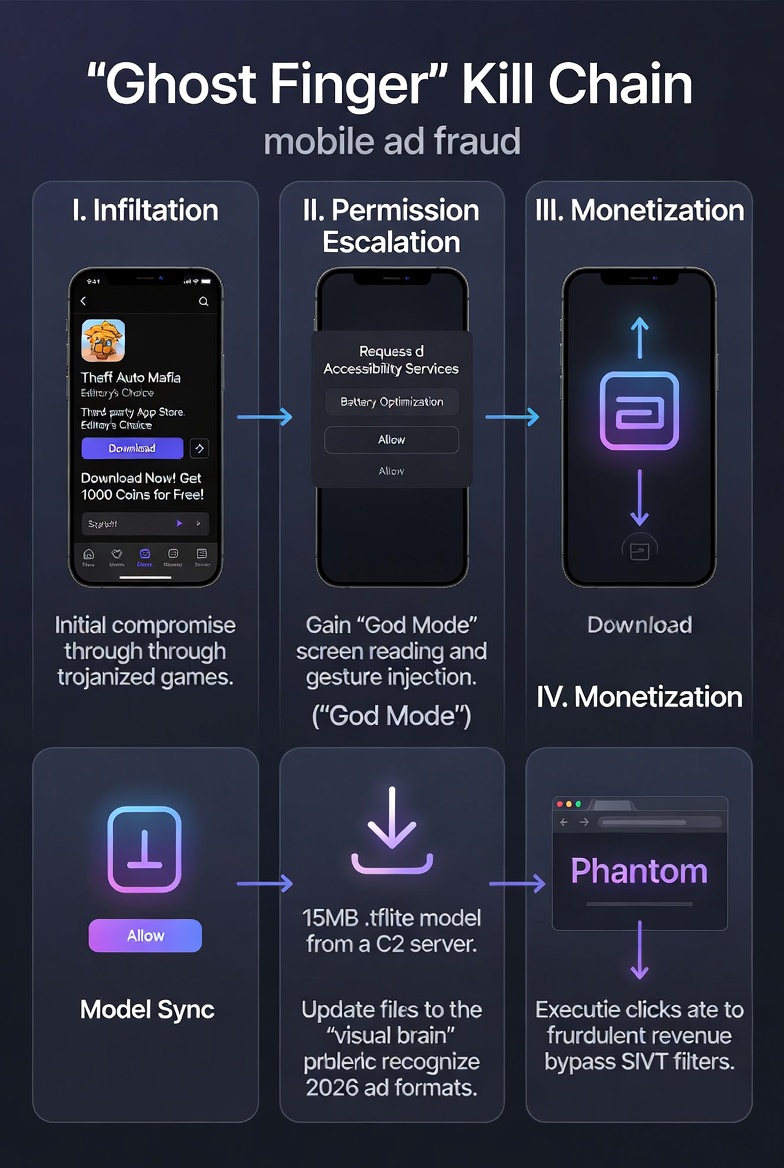
The "Ghost Finger" Kill Chain
| Phase | Action | Tactical Goal |
| I. Infiltration | Distributed via "Trojanized" games (e.g., Theft Auto Mafia) on third-party stores. | Establish initial foothold via "Editor’s Choice" lures. |
| II. Permission Escalation | Requests Accessibility Services under the guise of "Battery Optimization." | Gain "God Mode" to read the screen and inject gestures. |
| III. Model Sync | Downloads a 15MB .tflite model from a C2 server. | Update the "visual brain" to recognize the latest 2026 ad formats. |
| IV. Monetization | Executes clicks in a background "Phantom" browser. | Generate fraudulent revenue while bypassing SIVT (Sophisticated Invalid Traffic) filters. |
Operational & Financial Impact
Device Health: Rapid battery degradation and CPU thermal throttling due to constant background NPU/GPU usage.
Network Costs: High data consumption (exceeding 2GB/day in some cases) as the malware loads high-definition video ads in hidden layers.
Ecosystem Trust: Massive financial "drain" on digital advertisers, with 2026 projections estimating $172B in global losses attributed to AI-driven click fraud.
Remediation & Hardening (CyberDudeBivash™ Protocol)
Immediate Incident Response
Accessibility Audit: Immediately navigate to
Settings > Accessibility. Revoke permissions for any app that is not a verified system utility.Display Overlays: Check
Special App Access > Display Over Other Apps. Any "utility" or "game" with this permission should be considered compromised.Cache Purge: Clear the data and cache for all installed browsers to remove stored malicious JavaScript loaders.
Professional Hardening
NPU Monitoring: Implement EDR (Endpoint Detection & Response) that monitors Neural Processing Unit (NPU) spikes. Sudden AI-compute activity when the screen is off is a primary Indicator of Compromise (IoC).
Network Layer Filtering: Block known C2 domains associated with ClickWise, specifically those utilizing
tempisite.comorliveupdt[.]comfor model delivery.Zero Trust Mobile: Transition corporate fleets to "Managed Work Profiles" where Accessibility API requests require MDM (Mobile Device Management) approval.
YARA Rule 1: Detection of Embedded AI-Fraud Models
This rule targets the specific "Visual Brain" of the malware—the
.tflite(TensorFlow Lite) models optimized for recognizing UI elements like "X" buttons and ad-frames.Code snippetrule ClickWise_AI_Model_Detection { meta: author = "CyberDudeBivash" description = "Detects embedded TFLite models used for AI-driven ad-element recognition" threat_level = "Critical" date = "2026-01-22" strings: // TensorFlow Lite Magic Header $tflite_header = { 54 46 4C 33 } // "TFL3" // Semantic markers for UI element recognition $label_1 = "close_button" nocase $label_2 = "ad_frame" nocase $label_3 = "skip_ad" nocase $label_4 = "interstitial_overlay" nocase condition: $tflite_header at 0 and 2 of ($label_*) }YARA Rule 2: Accessibility Service & Gesture Injection Abuse
This rule identifies APKs that combine Accessibility Service permissions with low-level gesture injection strings, which are used to simulate human-like "Ghost Clicking."
Code snippetrule GhostFinger_Gesture_Injection { meta: author = "CyberDudeBivash" description = "Identifies apps combining Accessibility Services with automated gesture injection" incident_id = "2026-ADV-04-GF" strings: // Android Manifest permission string $perm_accessibility = "android.permission.BIND_ACCESSIBILITY_SERVICE" // Methods used for simulating human-like movement $click_method_1 = "dispatchGesture" $click_method_2 = "AccessibilityNodeInfo.ACTION_CLICK" // Behavioral masking strings (Human-jitter simulation) $jitter_log = "Randomizing tap duration" nocase $jitter_log_2 = "Human-mimic delay" nocase condition: $perm_accessibility and (any of ($click_method_*) and any of ($jitter_log_*)) }YARA Rule 3: Hidden WebView & C2 Model Delivery
The Ghost Finger strain uses a "Phantom Browser" (hidden WebView) to load ads. This rule detects the hidden rendering logic used to execute fraud while the screen is ostensibly off.
Code snippetrule ClickWise_Phantom_Browser { meta: author = "CyberDudeBivash" description = "Detects hidden WebView overlays used for unauthenticated ad-loading" strings: // Hidden WebView indicators $wv_hidden = "setAlpha(0.0f)" $wv_invisible = "setVisibility(View.INVISIBLE)" $wv_offscreen = "setTranslationX(-1000)" // C2 domain patterns for 2026-gen ClickWise $c2_pattern = /https?:\/\/[a-z0-9\-]+\.(tempisite|liveupdt|dealctr)\.com/ condition: (any of ($wv_*)) and $c2_pattern }How to Deploy (The "CyberDudeBivash" Implementation)
Scan APK Repositories: Use these rules with
yara-pythonor the YARA CLI to audit all third-party APKs before they are allowed on the corporate network.yara -r ClickWise_Master.yar /path/to/apk/repo
EDR Integration: If your mobile EDR supports YARA (like some 2026 versions of SentinelOne Mobile), upload these rules to detect "ClickWise" payloads dynamically in the
/data/app/directories.False Positive Note: Rule #1 might flag legitimate AI apps. Always cross-reference with Rule #2. If a "Calculator" app matches both, it is 100% malicious
This Python-based scanner is designed to crawl your internal application servers, unpack APKs (where necessary), and run the YARA rules we generated to identify the ClickWise AI (Ghost Finger) infection.
The "CyberDudeBivash" Automator: APK Neural Scanner

This script utilizes the
yara-pythonlibrary andosmodule to perform high-speed recursive scanning of your app repositories.Pythonimport yara import os import sys # CyberDudeBivash™ Tactical Script - 2026-CHL-SCAN # Automates detection of AI-driven clickers in APK repositories # 1. Path to your YARA rules file RULES_PATH = 'ClickWise_Master.yar' # 2. Directory containing your internal APKs TARGET_DIR = '/var/www/internal_apps/repos/' # 3. Log file for detections LOG_FILE = 'ghost_finger_detections.log' def compile_rules(): try: print(f"[*] Compiling CyberDudeBivash™ Tactical Rules: {RULES_PATH}...") return yara.compile(filepath=RULES_PATH) except Exception as e: print(f"[!] Compilation Error: {e}") sys.exit(1) def scan_repository(rules): print(f"[*] Starting scan in: {TARGET_DIR}") print("-" * 50) with open(LOG_FILE, 'a') as log: for root, dirs, files in os.walk(TARGET_DIR): for file in files: # Target APKs and raw dex/binary files if file.endswith(('.apk', '.dex', '.tflite')): file_path = os.path.join(root, file) matches = rules.match(file_path) if matches: alert = f"[!!!] THREAT DETECTED: {file_path} | Matches: {matches}\n" print(alert.strip()) log.write(alert) else: # Optional: Print progress for clean files print(f"[+] Clean: {file}") if __name__ == "__main__": if not os.path.exists(RULES_PATH): print(f"[!] Error: {RULES_PATH} not found.") sys.exit(1) compiled_rules = compile_rules() scan_repository(compiled_rules) print("-" * 50) print(f"[*] Scan Complete. Results saved to {LOG_FILE}")Tactical Deployment Guide
Environment Setup: Ensure you have the YARA library installed on your scanning server:
pip install yara-pythonPermissions: Run the script with the necessary permissions to read the
/var/www/or your specific repository mount point.Recursive Depth: The
os.walkfunction ensures that even if developers have nested APKs inside subdirectories or backup folders, the scanner will find them.Integration: You can easily add a
requests.postcall inside theif matches:block to send an instant alert to your Slack or Microsoft Teams security channel.
CyberDudeBivash’s Final Warning
In 2026, malware authors often use APK Packing (obfuscation) to hide strings. If this script returns "Clean" but you still see suspicious NPU activity in your telemetry, you may need to use an unpacker (like jadx or apktool) to decompress the APKs into raw source code before running the scanner.
CYBERDUDEBIVASH'S TIPS:
"CyberDudeBivash’s Pro-Tip: Hunting the Ghost in the Logs" If you are analyzing a suspected device, look for abnormal AccessibilityEvent logs. Specifically, look for
TYPE_VIEW_CLICKEDevents occurring when thePowerManager.isInteractive()state is FALSE.Command to check for Ghost Finger interaction via ADB:
adb shell dumpsys accessibility | grep -E "lastEventTime|packageName"If you see hundreds of click events registered while the screen was off/locked, you have identified a Ghost Finger infection.
IMPORTANT NOTE :
"The $172B Ad-Tech Meltdown" This isn't just a "virus" - it's an economic weapon. Gartner reports suggest that by mid-2026, AI-driven ad fraud like ClickWise AI will cause a 30% collapse in mobile ad-spend confidence. Small app developers are seeing their ad accounts banned by Google and Meta because the "traffic" from their users looks real, but never converts. The malware isn't just stealing battery life; it’s bankrupting the mobile ecosystem.
Explore the CYBERDUDEBIVASH® Ecosystem - a global cybersecurity authority delivering
Advanced Security Apps, AI-Driven Tools, Enterprise Services, Professional Training, Threat Intelligence, and High-Impact Cybersecurity Blogs.
Flagship Platforms & Resources
Top 10 Cybersecurity Tools & Research Hub
https://cyberdudebivash.github.io/cyberdudebivash-top-10-tools/
CYBERDUDEBIVASH Production Apps Suite (Live Tools & Utilities)
https://cyberdudebivash.github.io/CYBERDUDEBIVASH-PRODUCTION-APPS-SUITE/
Complete CYBERDUDEBIVASH Ecosystem Overview
https://cyberdudebivash.github.io/CYBERDUDEBIVASH-ECOSYSTEM
Official CYBERDUDEBIVASH Portal
https://cyberdudebivash.github.io/CYBERDUDEBIVASH
Official Website: https://www.cyberdudebivash.com
CYBERDUDEBIVASH® - Official GitHub | Production-Grade Cybersecurity Tools,Platforms,Services,Research & Development Platform
https://github.com/cyberdudebivash
https://github.com/apps/cyberdudebivash-security-platform
https://www.patreon.com/c/CYBERDUDEBIVASH
https://github.com/cyberdudebivash-pvt-ltd
Blogs & Research:
https://cyberbivash.blogspot.com
https://cyberdudebivash-news.blogspot.com
https://cryptobivash.code.blog
Discover in-depth insights on Cybersecurity, Artificial Intelligence, Malware Research, Threat Intelligence & Emerging Technologies.
Zero-trust, enterprise-ready, high-detection focus , Production Grade , AI-Integrated Apps , Services & Business Automation Solutions.
Star the repos → https://github.com/cyberdudebivash
Premium licensing & collaboration: DM or iambivash@cyberdudebivash.com
CYBERDUDEBIVASH
Global Cybersecurity Tools,Apps,Services,Automation,R&D Platform
Bhubaneswar, Odisha, India | © 2026
www.cyberdudebivash.com
2026 CyberDudeBivash Pvt. Ltd.
#CyberSecurity #AndroidSecurity #GhostFinger #ClickWiseAI #TechNews #MobileSafety #DigitalPrivacy #MalwareAlert #CyberDudeBivash


.jpg)
Comments
Post a Comment